Introduction
APIs play a crucial role in connecting cloud applications, but they are also prime targets for hackers. If APIs are not secured properly, they can lead to data breaches, service disruptions, and loss of customer trust.
Many security incidents happen due to common issues like misconfigured APIs, weak authentication, and vulnerabilities in API gateways. As more businesses rely on cloud services, API security must be a priority, not an afterthought.
This guide explains common API vulnerabilities and provides practical tips to secure your APIs and protect your data.
Why APIs Are at Risk
APIs are often targeted by hackers because they provide access to sensitive data. Most security breaches happen due to basic flaws like weak security design, poor encryption, and inadequate login systems.
The Most Common Attack Methods Include:
- Bypassing access controls to reach restricted API endpoints
- Exploiting excessive data exposure to retrieve sensitive information
- Injection attacks that manipulate the API to execute harmful commands
- Weak authentication that allows attackers to impersonate legitimate users
- Intercepting API communications to steal data or credentials
These weaknesses make it easy for attackers to access private information, putting businesses and customers at risk.
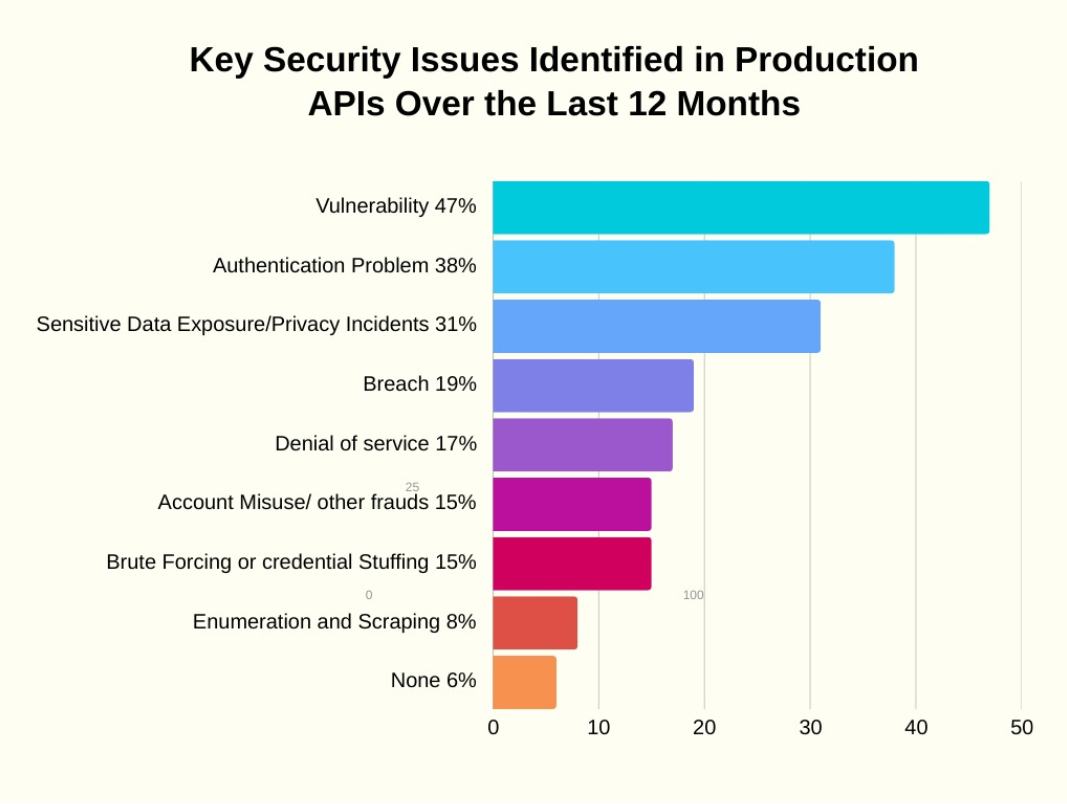
Common API Security Risks
- Broken Access Control – Attackers gain access to restricted API areas.
- Excessive Data Exposure – APIs reveal too much information, increasing security risks.
- Injection Attacks – Malicious code is injected through input fields.
- Weak Authentication – Insufficient mechanisms allow unauthorized access.
- Man-in-the-Middle Attacks – Attackers intercept API communication.
- Rate Limiting Abuse – APIs are overloaded to cause denial of service.
- Parameter Tampering – Parameters are manipulated to change API behavior.
- API Key Theft – Attackers steal keys to access APIs.
- Forced Browsing – Attackers access unauthorized parts of the API.
- Session Hijacking – Sessions are taken over by attackers.
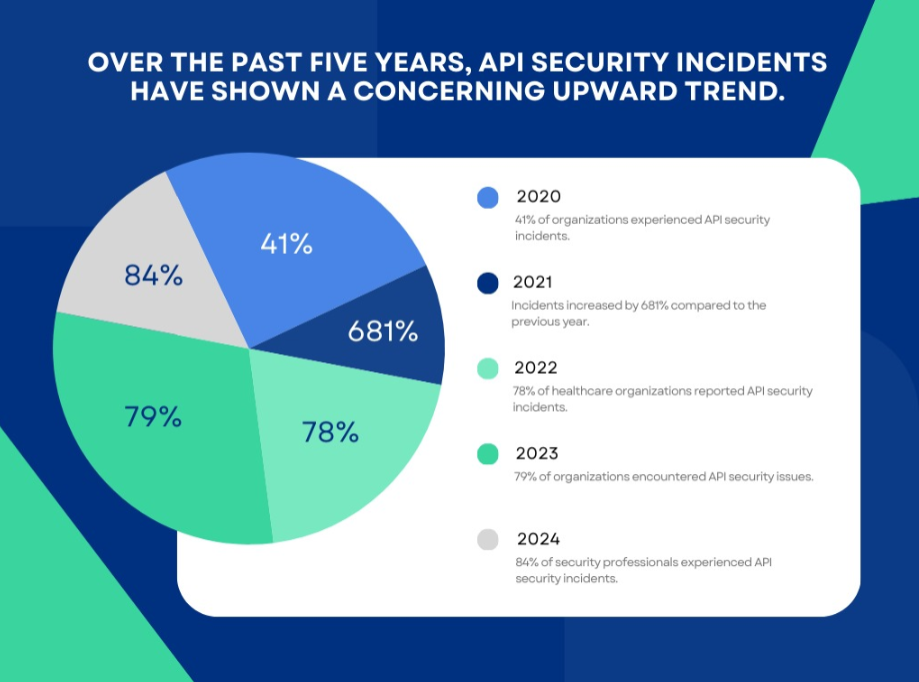

 Aug 9, 2025
Aug 9, 2025